ETHH: Exploring the Evolving Panorama of Moral Hacking and its Affect
Associated Articles: ETHH: Exploring the Evolving Panorama of Moral Hacking and its Affect
Introduction
On this auspicious event, we’re delighted to delve into the intriguing subject associated to ETHH: Exploring the Evolving Panorama of Moral Hacking and its Affect. Let’s weave attention-grabbing data and supply recent views to the readers.
Desk of Content material
ETHH: Exploring the Evolving Panorama of Moral Hacking and its Affect

The digital world, a tapestry woven with intricate threads of code and knowledge, is more and more susceptible to malicious actors. Cybersecurity threats are evolving at an alarming price, demanding subtle protection mechanisms. Enter moral hacking, a subject sometimes called penetration testing or white-hat hacking, which performs an important function in bolstering on-line safety. This text delves into the multifaceted world of moral hacking (ETHH), analyzing its core rules, methodologies, evolving panorama, authorized and moral issues, and its influence on the broader cybersecurity ecosystem.
Understanding the Fundamentals of ETHH:
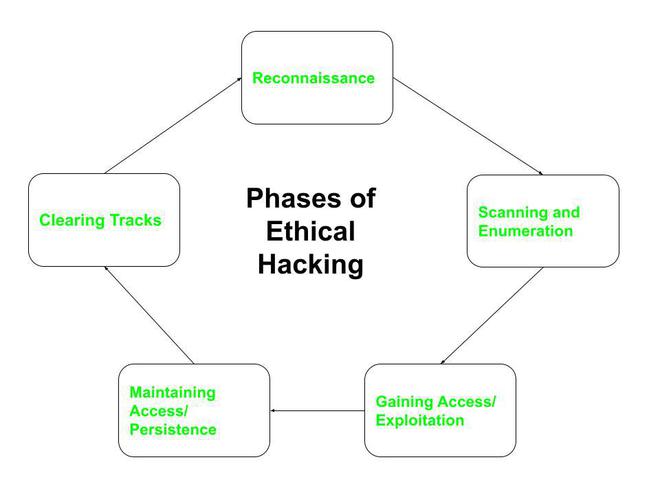
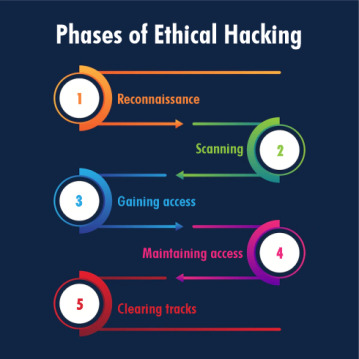
Moral hacking is the observe of utilizing hacking strategies to establish vulnerabilities in laptop techniques, networks, and functions. Not like malicious hackers (black-hats), who exploit vulnerabilities for private acquire or malicious intent, moral hackers work with the permission of the system proprietor to uncover weaknesses and suggest options to mitigate dangers. Their aim is to not trigger harm however to proactively strengthen safety postures. This entails a scientific strategy of figuring out, assessing, and reporting vulnerabilities earlier than malicious actors can exploit them.
The core rules guiding ETHH professionals embrace:
- Legality and Authorization: All actions have to be carried out with express written permission from the system proprietor. Unauthorized entry is unlawful and ethically reprehensible.
- Transparency and Disclosure: Moral hackers have to be clear about their actions and findings, offering detailed experiences to the system proprietor.
- Non-Malicious Intent: The first goal is to enhance safety, to not trigger hurt or disruption.
- Professionalism and Confidentiality: Moral hackers should preserve a excessive degree of professionalism, respecting confidentiality agreements and dealing with delicate data responsibly.
- Steady Studying: The cybersecurity panorama is consistently evolving, requiring moral hackers to constantly replace their expertise and information.
Methodologies Employed in ETHH:
ETHH professionals make the most of a variety of methodologies to evaluate safety vulnerabilities. These typically contain a mixture of automated instruments and guide strategies, relying on the precise scope of the engagement. Widespread methodologies embrace:
- Vulnerability Scanning: Automated instruments are used to scan techniques for recognized vulnerabilities, corresponding to outdated software program, weak passwords, and misconfigurations.
- Penetration Testing: This entails simulating real-world assaults to establish exploitable vulnerabilities. Penetration checks could be black-box (tester has no prior information), white-box (tester has full information), or grey-box (tester has partial information).
- Social Engineering: This method entails manipulating people to realize entry to delicate data or techniques. Moral hackers use this to evaluate the human aspect of safety.
- Community Mapping: Figuring out the construction and parts of a community to know its vulnerabilities.
- Wi-fi Safety Assessments: Evaluating the safety of wi-fi networks, together with entry factors and encryption protocols.
- Internet Utility Safety Testing: Figuring out vulnerabilities in internet functions, corresponding to SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Cellular Utility Safety Testing: Assessing the safety of cell functions, together with knowledge safety and entry controls.
The Evolving Panorama of ETHH:
The sector of ETHH is consistently evolving in response to the ever-changing risk panorama. A number of key traits are shaping the way forward for this essential career:
- Elevated Automation: The usage of automated instruments is rising, enabling sooner and extra environment friendly vulnerability assessments. This permits moral hackers to cowl a wider assault floor.
- Deal with Cloud Safety: With the rising adoption of cloud computing, there’s a rising demand for moral hackers specializing in cloud safety assessments.
- Rise of IoT Safety: The proliferation of Web of Issues (IoT) gadgets introduces new safety challenges, requiring specialised experience in IoT safety testing.
- AI and Machine Studying: AI and machine studying are getting used to boost vulnerability detection and risk prediction. Moral hackers are incorporating these applied sciences into their workflows.
- DevSecOps Integration: The combination of safety into the software program improvement lifecycle (DevSecOps) is changing into more and more necessary, requiring collaboration between builders and safety professionals.
Authorized and Moral Concerns:
Whereas ETHH is a vital part of cybersecurity, it is vital to function inside a strict authorized and moral framework. A number of key issues embrace:
- Written Consent: Specific written permission from the system proprietor is paramount. Lack of consent can result in critical authorized repercussions.
- Scope Definition: Clearly defining the scope of the engagement is important to keep away from exceeding licensed boundaries.
- Knowledge Privateness: Moral hackers should adhere to knowledge privateness rules, corresponding to GDPR and CCPA, when dealing with delicate data.
- Non-Disclosure Agreements (NDAs): NDAs are continuously used to guard delicate data uncovered in the course of the evaluation.
- Reporting Necessities: Detailed experiences outlining findings, vulnerabilities, and remediation suggestions have to be supplied to the system proprietor.
Affect of ETHH on the Cybersecurity Ecosystem:
ETHH performs an important function in strengthening the general safety posture of organizations and people. Its influence could be seen in a number of areas:
- Proactive Threat Mitigation: By figuring out vulnerabilities earlier than malicious actors, ETHH helps organizations proactively mitigate dangers and forestall expensive breaches.
- Improved Safety Consciousness: The method of penetration testing can spotlight weaknesses in safety consciousness coaching packages, resulting in improved worker schooling.
- Enhanced Safety Architectures: Findings from moral hacking assessments can inform the design and implementation of extra strong safety architectures.
- Compliance and Auditing: ETHH performs an important function in serving to organizations adjust to business rules and safety requirements.
- Financial Advantages: By stopping knowledge breaches and system failures, ETHH contributes to vital value financial savings for organizations.
Conclusion:
Moral hacking is a essential part of the fashionable cybersecurity panorama. Because the digital world turns into more and more complicated and interconnected, the demand for expert moral hackers will solely proceed to develop. By adhering to strict moral rules, using superior methodologies, and staying abreast of evolving threats, ETHH professionals play an important function in defending people and organizations from the ever-present risks of cyberattacks. The way forward for ETHH lies in embracing new applied sciences, collaborating throughout disciplines, and constantly adapting to the ever-shifting panorama of cybersecurity. The continued evolution of this subject ensures that the combat in opposition to cybercrime stays a dynamic and essential endeavor, safeguarding the integrity and safety of our more and more digital world.






Closure
Thus, we hope this text has supplied invaluable insights into ETHH: Exploring the Evolving Panorama of Moral Hacking and its Affect. We respect your consideration to our article. See you in our subsequent article!